For no apparent reason Java got corrupted in my machine. One can fully expect this as when Java updates itself, it leaves a significant amount of "junk" from the old version. It will still work.. But for some unknown and unexplainable reason, it doesn't work now. So the quest to put its services back begins..
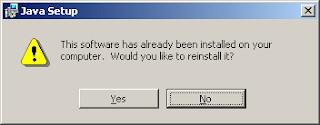
I uninstalled the Java software from the "Add/Remove Programs" menu of the control panel and it was "uninstalled" as expected. So I downloaded the latest and greatest version off its website.. And, while trying to re-install it, I realized that was not the case -- Java was still installed (as seen on the screenshot below).
And while clicking "Yes", I got prompted with another error:
The second error made more sense as I had intentionally uninstalled the software. But why does the installer think that Java is still installed? It is due to a registry entry that got left over from the previous Java installation (which the uninstall did not get rid of).
As "Administrator" or a user that is a member of the "Administrators" group, open the registry editor and browse over to this key and delete it:
or save the code below as a .reg file and merge to your registry..
Then try to re-install Java. It should now be able to install without hitch.
The uninstaller should have taken care of this simple problem. And for a widely used software like Java a simple matter like this should not add to your headaches.
I uninstalled the Java software from the "Add/Remove Programs" menu of the control panel and it was "uninstalled" as expected. So I downloaded the latest and greatest version off its website.. And, while trying to re-install it, I realized that was not the case -- Java was still installed (as seen on the screenshot below).
And while clicking "Yes", I got prompted with another error:
This action is only valid for products that are currently installed.
The second error made more sense as I had intentionally uninstalled the software. But why does the installer think that Java is still installed? It is due to a registry entry that got left over from the previous Java installation (which the uninstall did not get rid of).
As "Administrator" or a user that is a member of the "Administrators" group, open the registry editor and browse over to this key and delete it:
HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Runtime Environment
or save the code below as a .reg file and merge to your registry..
;--- start of code ---
Windows Registry Editor Version 5.00
[-HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Runtime Environment]
;--- end of code ---
Then try to re-install Java. It should now be able to install without hitch.
The uninstaller should have taken care of this simple problem. And for a widely used software like Java a simple matter like this should not add to your headaches.