I use a Raspberry PI (RPI) at home. I have blogged several times about my adventures with the RPI and some automation that I programmed in. It is currently running a very lightweight and optimized version of Linux named DietPI. The RPI is cheap. It operates cheap, since it doesn't consume a lot of electricity meaning I could leave it running headless 24x7x365. The only time it reboots is if there are critical updates that require it.
Since it is running 24x7, the RPI could also serve as my SSH tunnel to my home network from the internet. I use ngrok to achieve this and forward the SSHD port to the tunnel server. Ngrok does not run in daemon-mode and the developer has expressed that this feature will not be built-into the software. But on Linux this is not a really problem.
A supervisor could handle the software and even restart it if necessary. This is how I did it on my RPI.
First, install supervisor and download the latest version of ngrok.
Download ngrok off its developer's website, https://ngrok.com/download. Choose Linux ARM. Extract the contents of the zip file and copy it to /usr/local/bin. While in the ngrok website, register and obtain an authtoken.
Next, generate the default ngrok configuration file by running:
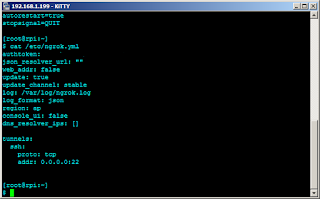
A configuration file will be generated in $HOME/.ngrok2/ngrok.yml. I modified this configuration file and copied it to /etc. The entire contents of my ngrok.yml is below.
On to supervisor configuration. Create the configuration file as follows:
Then, set supervisor to autostart at boot.
To check the status of supervisor controlled daemons, run..
Check the dashboard on the ngrok website to see how you could connect to the tunnel from any internet connection.
RELATED: Root Backdoor to VMware ESXi Host
The best part is: this configuration doesn't have to modify firewall configurations nor forward ports on the router.
Since it is running 24x7, the RPI could also serve as my SSH tunnel to my home network from the internet. I use ngrok to achieve this and forward the SSHD port to the tunnel server. Ngrok does not run in daemon-mode and the developer has expressed that this feature will not be built-into the software. But on Linux this is not a really problem.
A supervisor could handle the software and even restart it if necessary. This is how I did it on my RPI.
First, install supervisor and download the latest version of ngrok.
apt-get -y install supervisor
Download ngrok off its developer's website, https://ngrok.com/download. Choose Linux ARM. Extract the contents of the zip file and copy it to /usr/local/bin. While in the ngrok website, register and obtain an authtoken.
Next, generate the default ngrok configuration file by running:
/usr/local/bin/ngrok authtoken [putyourownauthtokenhere]
A configuration file will be generated in $HOME/.ngrok2/ngrok.yml. I modified this configuration file and copied it to /etc. The entire contents of my ngrok.yml is below.
On to supervisor configuration. Create the configuration file as follows:
[program:ngrok] command=/usr/local/bin/ngrok start --all --config=/etc/ngrok.yml autostart=true autorestart=true stopsignal=QUIT
Then, set supervisor to autostart at boot.
systemctl enable supervisor systemctl start supervisor
To check the status of supervisor controlled daemons, run..
supervisorctl status
Check the dashboard on the ngrok website to see how you could connect to the tunnel from any internet connection.
RELATED: Root Backdoor to VMware ESXi Host
The best part is: this configuration doesn't have to modify firewall configurations nor forward ports on the router.