They say that most of the world will be connected via the global information highway or what is known as the internet soon. While technology is getting there, a burgeoning problem seems to emerge. The communication layer known as IPv4 (which we commonly know as the "IP address") will run out before that prediction ever becomes a reality.
Its successor -- IPv6 -- has been here for years now and while the world has not wholly embraced the technology in the literal sense of the word, it is "better" and will inevitably succeed IPv4 in the near future. In fact, most of the modern operating systems we commonly use support IPv6 protocols. So why not give it a spin to get a real experience with what it does, right? In a nutshell IPv6 is:
Philippines is one of those countries who have not implemented IPv6 just yet. ISPs here stick to IPv4. So if your current location has no support for IPv6, how do you take advantage of this technology? The answer is via IPv6 tunnelling. There are many ways of implementing tunneling. But here, we focus on gogo6 client. Download the required software from its webpage, then go ahead and install it.
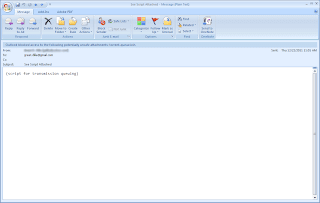
Launch the gogoCLIENT utility. Under the "Basic" tab, tick Connect Anonymously and connect to server "anonymous.freenet6.net". You should be having a similar screenshot as below.
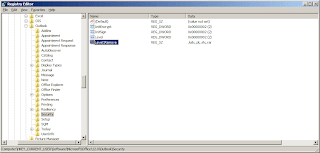
Now go to the "Advanced" tab. Set Tunnel Mode to "IPV6-in-UDP-IPV4 Tunnel (NAT Traversal)". Tunnel Authentication Mode should remain "Anonymous" (this is set to Anonymous by default).
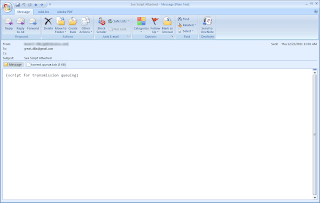
Go back to the "Basic" tab and click Connect. You should be able to connect to the nearest freenet6 server on your current location. On the "Status" tab, you will be able to see connection details.
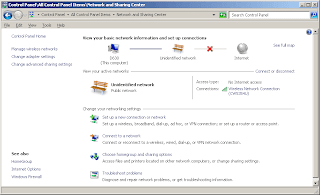
Once successful, your computer can now connect to multiple IPv6 websites. To test this, browse google's IPv6 search page via http://ipv6.google.com.
The above procedure is what I followed to get IPv6 working on my desktop. It is running Windows 7 x64 Ultimate. As always, your mileage may vary.
Its successor -- IPv6 -- has been here for years now and while the world has not wholly embraced the technology in the literal sense of the word, it is "better" and will inevitably succeed IPv4 in the near future. In fact, most of the modern operating systems we commonly use support IPv6 protocols. So why not give it a spin to get a real experience with what it does, right? In a nutshell IPv6 is:
Internet Protocol version 6 (IPv6) is a version of the Internet Protocol (IP). It is designed to succeed the Internet Protocol version 4 (IPv4). The Internet operates by transferring data between hosts in small packets that are independently routed across networks as specified by an international communications protocol known as the Internet Protocol.
Each host or computer on the Internet requires an IP address in order to communicate. The growth of the Internet has created a need for more addresses than are possible with IPv4. IPv6 was developed by the Internet Engineering Task Force (IETF) to deal with this long-anticipated IPv4 address exhaustion, and is described in Internet standard document RFC 2460, published in December 1998.[1] Like IPv4, IPv6 is an internet-layer protocol for packet-switched internetworking and provides end-to-end datagram transmission across multiple IP networks. While IPv4 allows 32 bits for an Internet Protocol address, and can therefore support 232 (4,294,967,296) addresses, IPv6 uses 128-bit addresses, so the new address space supports 2128 (approximately 340 undecillion or 3.4×1038) addresses. This expansion allows for many more devices and users on the internet as well as extra flexibility in allocating addresses and efficiency for routing traffic. It also eliminates the primary need for network address translation (NAT), which gained widespread deployment as an effort to alleviate IPv4 address exhaustion.
-- taken from Wikipedia: IPv6
Philippines is one of those countries who have not implemented IPv6 just yet. ISPs here stick to IPv4. So if your current location has no support for IPv6, how do you take advantage of this technology? The answer is via IPv6 tunnelling. There are many ways of implementing tunneling. But here, we focus on gogo6 client. Download the required software from its webpage, then go ahead and install it.
Launch the gogoCLIENT utility. Under the "Basic" tab, tick Connect Anonymously and connect to server "anonymous.freenet6.net". You should be having a similar screenshot as below.
Now go to the "Advanced" tab. Set Tunnel Mode to "IPV6-in-UDP-IPV4 Tunnel (NAT Traversal)". Tunnel Authentication Mode should remain "Anonymous" (this is set to Anonymous by default).
Go back to the "Basic" tab and click Connect. You should be able to connect to the nearest freenet6 server on your current location. On the "Status" tab, you will be able to see connection details.
Once successful, your computer can now connect to multiple IPv6 websites. To test this, browse google's IPv6 search page via http://ipv6.google.com.
The above procedure is what I followed to get IPv6 working on my desktop. It is running Windows 7 x64 Ultimate. As always, your mileage may vary.