The reason I'm making this article is to make file sharing possible between Windows XP and Windows 7 computers. Although I'm not exactly sure if this was the reason behind the successful file sharing between computers, it probably contributed to the success.
Link Layer Topology Discovery (or LLTD) is not installed in Windows XP by default. It has to be installed to the target computer to enable the protocol. According to the microsoft website:
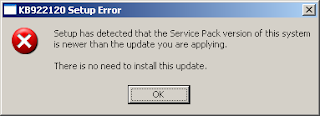
However, KB922120 (LLTD) is intended for Service Pack 2 (SP2) and it will not install on a computer with Service Pack 3 (SP3) installed. This error will appear when trying to install KB922120 on a computer with SP3 update (see screenshot).
Not to worry, the LLTD protocol can still be installed. Download KB92210 (WindowsXP-KB922120-v5-x86-ENU.exe) from microsoft webpage, or search for lltd and you will easily find the resource where it can be obtained. Validation is required to acquire the file.
Extract the file to a directory of your liking. For this article, we will extract the file to a directory named D:\922120. To extract, open a command terminal and execute:
The files included in the KB922120 update will then be present in D:\922120. Now copy the following files to their respective target directories:
When the files have been copied, execute:
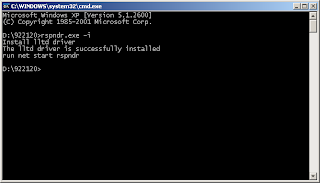
You will be getting a terminal window similar to one below (see screenshot).
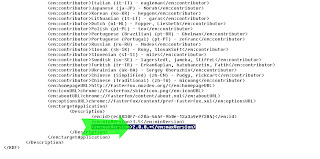
Link Layer Topology Discovery protocol should be enabled after this. If you check on of your network interfaces, the LLTD protocol should show up in its properties.
If you see a similar screenshot as above, LLTD is installed. There you go, installing LLTD on your Windows XP SP3 computer.
Link Layer Topology Discovery (or LLTD) is not installed in Windows XP by default. It has to be installed to the target computer to enable the protocol. According to the microsoft website:
This package contains the Link Layer Topology Discovery (LLTD) responder. The network map on a computer running Windows Vista shows a graphical view of the computers and devices on your network and how they are connected by using the LLTD protocol. The LLTD responder must be installed on a computer running Windows XP before it can be detected and appear on the network map. After you install this item, you may have to restart your computer.
However, KB922120 (LLTD) is intended for Service Pack 2 (SP2) and it will not install on a computer with Service Pack 3 (SP3) installed. This error will appear when trying to install KB922120 on a computer with SP3 update (see screenshot).
Not to worry, the LLTD protocol can still be installed. Download KB92210 (WindowsXP-KB922120-v5-x86-ENU.exe) from microsoft webpage, or search for lltd and you will easily find the resource where it can be obtained. Validation is required to acquire the file.
Extract the file to a directory of your liking. For this article, we will extract the file to a directory named D:\922120. To extract, open a command terminal and execute:
> WindowsXP-KB922120-v5-x86-ENU.exe -x
The files included in the KB922120 update will then be present in D:\922120. Now copy the following files to their respective target directories:
> rspndr.sys (D:\922120\SP2QFE) --> %WINDIR%\system32\drivers
> rspndr.exe (D:\922120\SP2QFE) --> %WINDIR%\system32
> rspndr.inf (D:\922120\SP2QFE\IP) --> %WINDIR%\inf
When the files have been copied, execute:
> rspndr.exe -i
You will be getting a terminal window similar to one below (see screenshot).
Link Layer Topology Discovery protocol should be enabled after this. If you check on of your network interfaces, the LLTD protocol should show up in its properties.
If you see a similar screenshot as above, LLTD is installed. There you go, installing LLTD on your Windows XP SP3 computer.