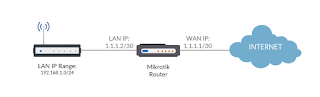
It is likely that your internet service provider (ISP) will not give you an entire block of IP addresses (otherwise, it will be a very expensive service). They expect you configure some form of network address translation in order to access the internet or traverse to another network. In order to understand the concepts, let us define the two common methods of NAT, which are source NAT (in Mikrotik lingo "srcnat") and destination NAT (in Mikrotik lingo "dstnat"). Just keep in mind that for connections bound to the internet (going out of the network), srcnat is involved; consequently, for connections going in to the local area network, it is dstnat.
NAT in this case does the one-to-many translations. As the traffic passes through the router bound for the internet, the router "masquerades" the IP address of the packet with the public IP address (refer to the initial configuration post) of the router (as additional reading references, you may want to checkout the RFC1918 standard). The router also performs another significant function of tracking the active connections. When inbound packets return, it uses this tracking information to determine the private IP address to forward the packets to.
Having mentioned that, there are two major configuration blocks that need to be added to the Mikrotik router. The NAT part and the firewall forward chain part. At your discretion, you may also want to adjust connection tracking parameters of the router, if the default configuration does not fit.
SRCNAT. First, source NAT or srcnat. Still taking into account the same configuration that we used in the previous articles. Given a static public IP address, srcnat is best deployed.
/ip firewall nat
add action=srcnat chain=srcnat out-interface=ether1 \
src-address=192.168.1.0/24 to-addresses=1.1.1.2
Another way of configuring this is to use another form of source NAT called "masquerade". Masquerade is a specialized form of srcnat. While srcnat requires a destination IP address, masquerade requires a specific interface and retrieves the IP address assigned to the interface when performing the NAT process. There is an associated overhead to masquerade due to this. Just know that in the absence of a static public IP, masquerade is the solution to go. Masquerade was created to work with dynamic IP addresses on the outbound interfaces.
/ip firewall nat
add action=masquerade chain=srcnat out-interface=ether1 \
src-address=192.168.1.0/24
Given a static public IP address on the outbound interface, both configurations will work. However, it is recommended to use the first configuration to minimize overhead. I have not tested how big the overhead is on my setup but I guess it will vary from setup to setup.
FORWARD chain. The router's built-in firewall needs to be instructed to forward packets NAT'd to the local area network. It needs to accept new connections initiated from the LAN as well.
/ip firewall filter
add chain=forward action=drop comment="DROP invalid packets" connection-state=invalid
add chain=forward action=accept comment="FORWARD packets from LAN" \
connection-state=related,established
This block of code needs to come after the input chain (router protection).
RELATED: Initial Configuration of a Mikrotik Virtual Router
There you go, after putting the above code in conjuction with the previous configurations done, you will now have a working router able to provide basic network connectivity plus internet access. Next we will discuss quality of service (QoS) or packet prioritization and bandwidth shaping on the Mikrotik router.