If you still haven't heard, there is a massive "ransomware" attack that is out there and organizations are starting to react to its effects. While you and I might not be the actual targets of this malware, you and I could still end up in its wake.. and worse, lose valuable data in the process.
The malware is well-known for "WannaCry", among other names. And what it does is encrypt your files asking for ransom in order to decrypt them (which is why it is called "ransomware"). You and I will then have a limited number of days to pay, or else the encrypted files are deleted.
This malware spreads itself across the network using a zero-day vulnerability which experts coined "EternalBlue". While Microsoft came out with the patch to address this vulnerability in its Windows Operating system, there are still a lot out there who are using both new and legacy unpatched systems, or are simply not aware of this existing threat.
If you have not done so, the link to the Windows patches is: Microsoft Security Bulletin 17-010 (Critical). In the essence of being informed, what WannaCry malware does is better explained in this youtube video: https://www.youtube.com/watch?v=88jkB1V6N9w.
Now if you have actually installed the updates and want to be sure, developers from a company Let's Get Digital came up with a tool to help you check systems. Download the software by clicking this link.
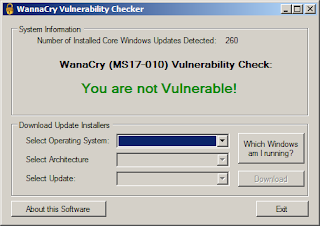
I tested it out on my computer. The result is in the screenshot below.
It seems the patches in place are keeping me safe (for now at least).
RELATED: Install Adblock on Raspberry Pi via Pi-Hole
Go ahead and install the patch immediately, if you haven't done so. As the saying goes, an ounce of prevention is better than... But you already know that right?
Subscribe for Latest Update
Popular Posts
-
One of the many obstacles facing the information technology growth in the Philippines is the high cost of ADSL or any other form of internet...
Post Labels
100gb
(1)
acceleration
(1)
acrobat
(1)
adblock
(1)
advanced
(1)
ahci
(1)
airdrop
(2)
aix
(14)
angry birds
(1)
article
(21)
aster
(1)
audiodg.exe
(1)
automatic
(2)
autorun.inf
(1)
bartpe
(1)
battery
(2)
bigboss
(1)
binance
(1)
biometrics
(1)
bitcoin
(3)
blackberry
(1)
book
(1)
boot-repair
(2)
calendar
(1)
ccleaner
(3)
chrome
(5)
cloud
(1)
cluster
(1)
compatibility
(3)
CPAN
(1)
crypto
(3)
cydia
(1)
data
(3)
ddos
(1)
disable
(1)
discount
(1)
DLNA
(1)
dmidecode
(1)
dns
(7)
dracut
(1)
driver
(1)
error
(10)
esxi5
(2)
excel
(1)
facebook
(1)
faq
(36)
faucet
(1)
firefox
(17)
firewall
(2)
flash
(5)
free
(3)
fun
(1)
gadgets
(4)
games
(1)
garmin
(5)
gmail
(3)
google
(4)
google+
(2)
gps
(5)
grub
(2)
guide
(1)
hardware
(6)
how
(1)
how-to
(45)
huawei
(1)
icloud
(1)
info
(4)
iphone
(7)
IPMP
(2)
IPV6
(1)
iscsi
(1)
jailbreak
(1)
java
(3)
kodi
(1)
linux
(28)
locate
(1)
lshw
(1)
luci
(1)
mafia wars
(1)
malware
(1)
mapsource
(1)
memory
(2)
mikrotik
(5)
missing
(1)
mods
(10)
mouse
(1)
multipath
(1)
multitasking
(1)
NAT
(1)
netapp
(1)
nouveau
(1)
nvidia
(1)
osmc
(1)
outlook
(2)
p2v
(2)
patch
(1)
performance
(19)
perl
(1)
philippines
(1)
php
(1)
pimp-my-rig
(9)
pldthomedsl
(1)
plugin
(1)
popcorn hour
(10)
power shell
(1)
process
(1)
proxy
(2)
pyspark
(1)
python
(13)
qos
(1)
raspberry pi
(7)
readyboost
(2)
reboot
(2)
recall
(1)
recovery mode
(1)
registry
(2)
rename
(1)
repository
(1)
rescue mode
(1)
review
(15)
right-click
(1)
RSS
(2)
s3cmd
(1)
salary
(1)
sanity check
(1)
security
(15)
sendmail
(1)
sickgear
(3)
software
(10)
solaris
(17)
squid
(3)
SSD
(3)
SSH
(9)
swap
(1)
tip
(4)
tips
(42)
top list
(3)
torrent
(5)
transmission
(1)
treewalk
(2)
tunnel
(1)
tweak
(4)
tweaks
(41)
ubuntu
(4)
udemy
(6)
unknown device
(1)
updates
(12)
upgrade
(1)
usb
(12)
utf8
(1)
utility
(2)
V2V
(1)
virtual machine
(4)
VirtualBox
(1)
vmware
(14)
vsphere
(1)
wannacry
(1)
wifi
(4)
windows
(54)
winpe
(2)
xymon
(1)
yum
(1)
zombie
(1)
RANDOM POSTS
-
the posts here are my own and not shared nor endorsed by the companies i am affiliated with.
i am a technologist who likes to automate and make things better and efficient. i can be reached via great [dot] dilla [at] gmail [dot] com.
if this post has helped, will you buy me coffee?