IP Spoofing is a technique used to gain unauthorized access to machines, whereby an attacker illicitly impersonate another machine by manipulating IP packets. IP Spoofing involves modifying the packet header with a forged (spoofed) source IP address, a checksum, and the order value.
As a responsible infrastructure administrator, I am obliged to contribute to the security of others. And with that, likewise share the same information on how to do it as well for others benefit. If you own a Mikrotik router, follow the procedure below.
RP Filter. The "RP Filter" is used for packet source validation. As defined in RFC3704 Abstract, it is designed to limit the impact of distributed denial of service attacks, by denying traffic with spoofed addresses access to the network, and to help ensure that traffic is traceable to its correct source network.
To be better informed about this change, here's a link to the Mikrotik Wiki.
So how is this done in the Mikrotik?
To those who want to do it via command line interface (CLI), execute this using a privileged account:
/ip settings set rp-filter=strict
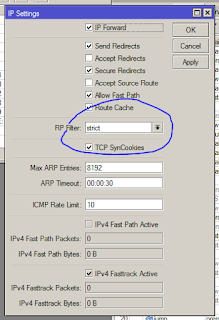
Those who would rather use WinBox utility, IP » Settings. Set "RP Filter" to "strict".
In the screenshot above, "TCP SynCookies" is ticked. This is a further router protection from DDoS via SYN floods. For the CLI equivalent to that, the CLI command above should be changed to:
/ip settings set rp-filter=strict tcp-syncookies=yes
RELATED: Mikrotik Articles in This Series
The above changes did not increase the resource consumption on my router. Monitor your router for changes to utilization of resources to see if the change does introduce significant load.