There are two-things most notable about opensource software -- active development from a community of users, and, the benefit of using something that comes free. However, the learning curve varies since the actual training itself (the immersion process) comes at a price. Sometimes discounted, but still with a price tag. Like the course that got me started with Python --
Complete Python Bootcamp: from Zero to Hero. Time and time again, you will hear me say this is what I highly recommend as a starting point.
In order to advance the building of knowledge and the immersion process of using Python, load up on advanced courses. One advanced course is being offered for free in Udemy. It is the course
Learn Advanced Python. I haven't taken this course yet, but I enrolled since it is being offered for free!
I have included a screenshot of what I'm seeing on screen from the link I posted above. Or simply click this thumbnail to follow the link. Go ahead as the embedded coupon code might expire soon.
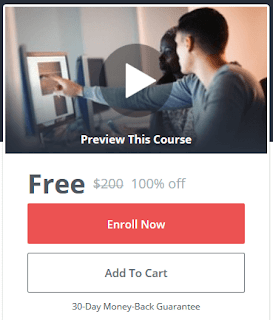
Completing a course in Udemy, comes with a certificate that you can use for credentials. In order to whet your appetite on what to expect, below is the course description:
Python is one of the most widely used high level programming language. The language stresses on code readability and due to its syntax and implementation a programmer has to write lesser code as compared to other languages such as C++ and Java. The language supports multiple style like functional programming, object oriented or imperative style. The memory management is done automatically and has many standard libraries available for python programmer.
Learning a programming language is always an uphill ride but as luck would favor us python was designed to be easily learnt by a novice programmer. Python code is readable and with a little knowledge a developer can learn many things just by looking at the code. It executes read evaluate print loop which gives developer a chance to play around with code and experiment. Also the standard library offers you a lot of functionalities which lets you execute complex functionalities with ease.
Learning python opens up many doors for python developers in the world of programming. Python has an object oriented approach which is preferred by many leading languages such as C#, Ruby, JavaScript, Perl etc. So once you get comfortable with the concepts of python you can switch to any other object oriented language and the only thing you will have to learn is the syntax of language.
To create a product which stands out amongst the crowd, you can develop it in any language. But there are certain constraints like time and budget which can’t be overlooked. This is where the choice of language decides the fate of the project and if project is big the company also might get affected. Python is a good choice for startups as it allows quick development and the amount of code is less as compared to c, java etc. Python can scale the most complex application effortlessly and can be handled by a small team effectively. Python also has a very reliable support team to solve your queries.
A python developer can rarely get stuck as there are large number of resources available which keeps on getting updated. It has a huge standard library which provides inbuilt functionality which is why some known applications are built on Python.
RELATED: Huge Discounts on Python Courses at Udemy
Hope this gets you going in your quest to add Python in your everyday go-to tools for the trade. Share with your friends who also want to learn and benefit from Python. If you wish to keep up to date with free and discounted Python courses by using the subscribe link in the right panel of the webpage.